house_of_apple2浅析
利用条件
- 泄露libc和heap地址
- 使用
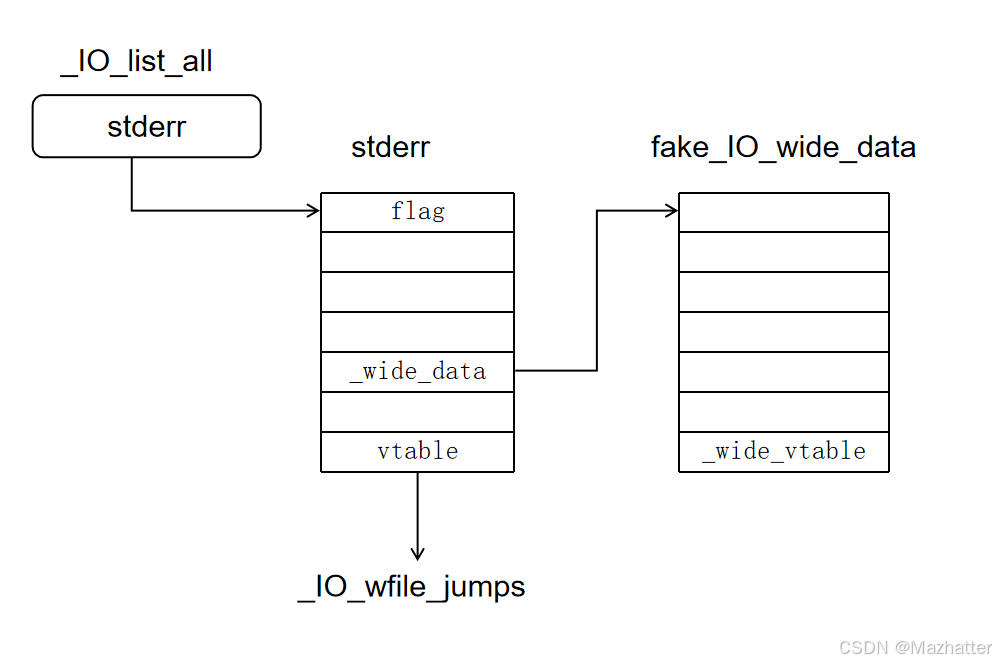
largebin attack控制_IO_list_all - 能控制程序执行
IO操作,包括但不限于:从main函数返回、调用exit函数
- 能控制程序执行
- 控制
fakeio_file的vtable和_wide_date
使用
_flags设置为~(2 | 0x8 | 0x800),如果不需要控制rdi,设置为0即可;如果需要获得shell,可设置为sh;,注意前面有两个空格vtable设置为_IO_wfile_jumps/_IO_wfile_jumps_mmap/_IO_wfile_jumps_maybe_mmap地址(加减偏移),使其能成功调用_IO_wfile_overflow即可_wide_data设置为可控堆地址A,即满足*(fp + 0xa0) = A_wide_data->_IO_write_base设置为0,即满足*(A + 0x18) = 0_wide_data->_IO_buf_base设置为0,即满足*(A + 0x30) = 0_wide_data->_wide_vtable设置为可控堆地址B,即满足*(A + 0xe0) = B_wide_data->_wide_vtable->doallocate设置为地址C用于劫持RIP,即满足*(B + 0x68) = C
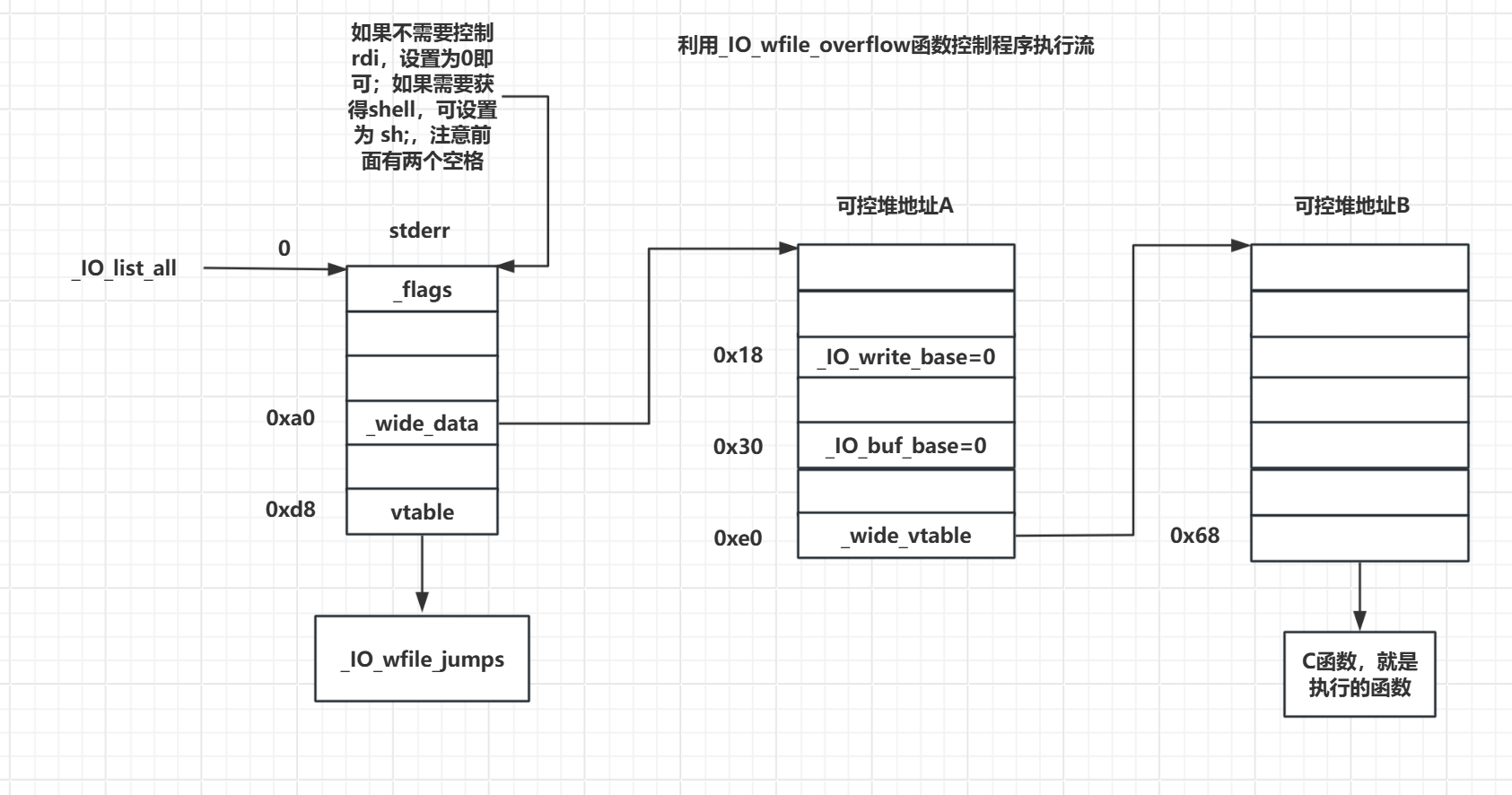
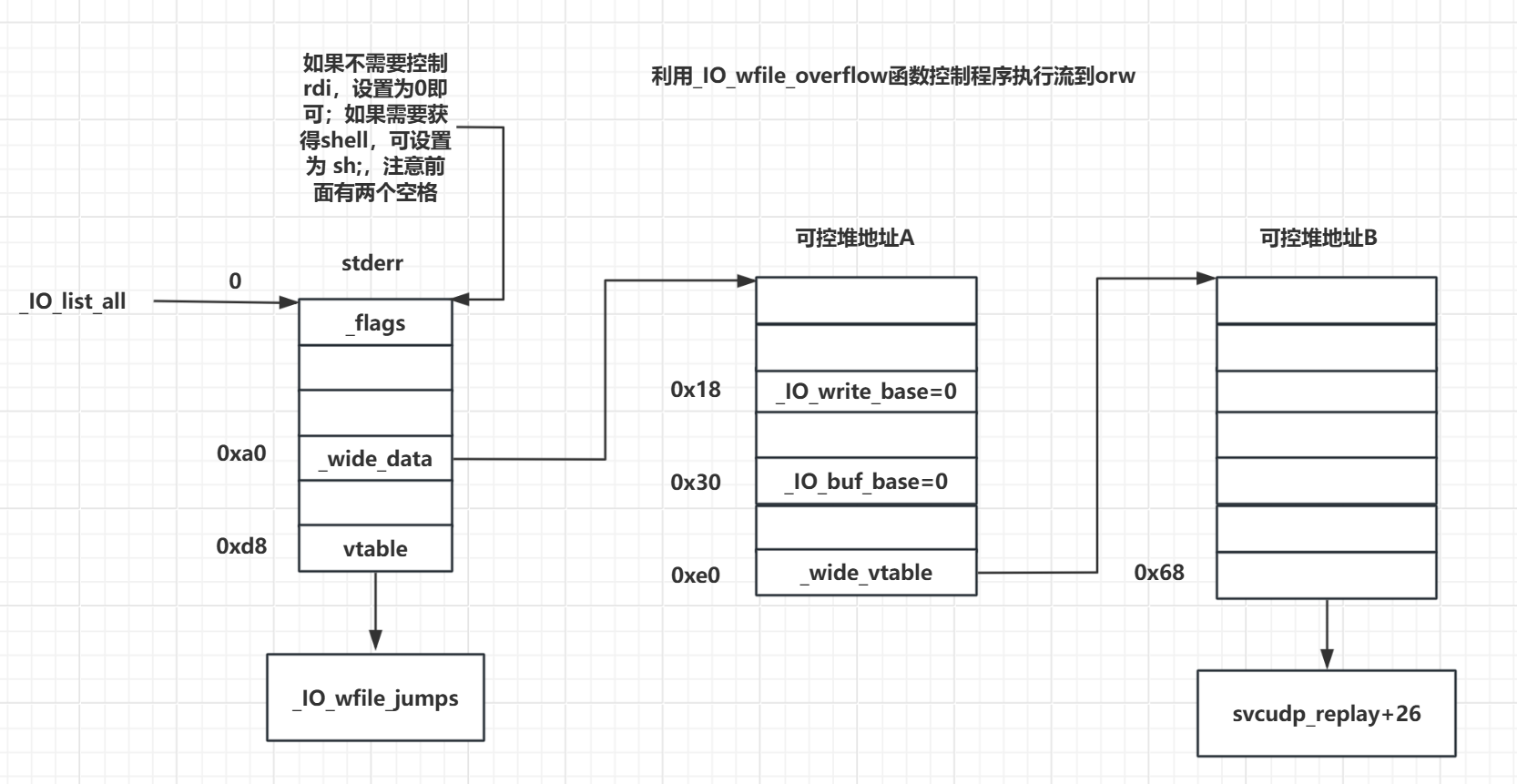
需要提前获取的参数
io_list_all = libc_base + libc.sym["_IO_list_all"] |
模板一shell
执行system("sh");
这样伪造比较简单。
fake_file = flat({ |
模版二orw(mprotect)
orw = p64(0) + p64(prdx_r12) + p64(0) + p64(fake_io_addr - 0x10) |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Ya0rk の Blog!
